MEC多接入边缘计算及关键技术
568 浏览 5 years, 8 months
4.2.7 Regulatory requirements
版权声明: 转载请注明出处 http://www.codingsoho.com/5G Lawful Interception (LI) and Retained Data (RD) continue to play a crucial role in helping Law Enforcement Agencies (LEAs) to combat terrorism and serious criminal activity. LI enables a LEA to perform electronic surveillance on an individual (a target) as authorized by a judicial or administrative order. To facilitate the lawful intercept process, certain legislation and regulations require service providers and Internet service providers to implement their networks to explicitly support authorized electronic surveillance. Actions taken by the service providers include: provisioning the target identity in the network to enable isolation of target communications (separating it from other users' communications), duplicating the communications for the purpose of sending the copy to the LEA, and delivering the Interception Product to the LEA.
In the context of MEC, it is recommended to utilise the LI&RD at SMF and UPF based on the CUPS LI model (Control and User Plane Separation of EPC nodes) as specified in 3GPP Rel-14. The figure below shows an example 5G LI model that is currently under discussion in 3GPP. As explained in the previous sections, the UPF is effectively the data plane for the MEC hosts, thus it is an integral part of the MEC deployment in a 5G network. Consequently, the 3GPP LI&RD is natively supported for MEC application traffic as it is for any application traffic passing the UPF.
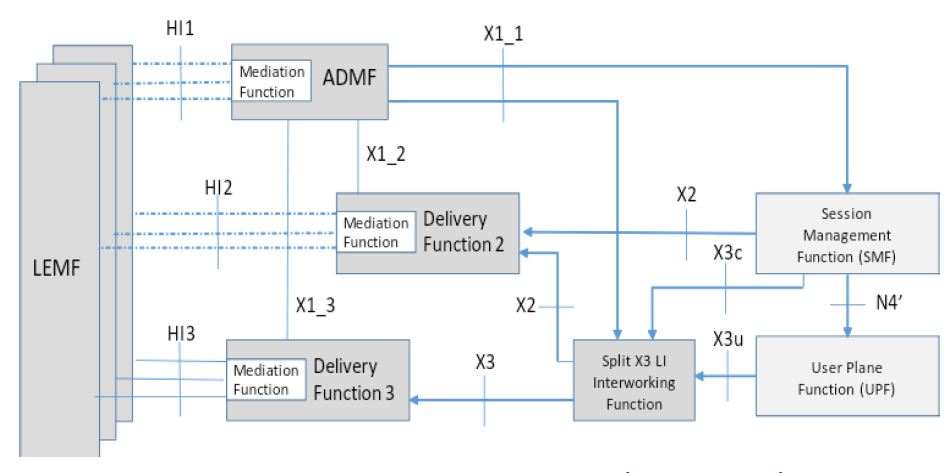
Figure 6. 5G Lawful Interception architecture (3GPP proposal).